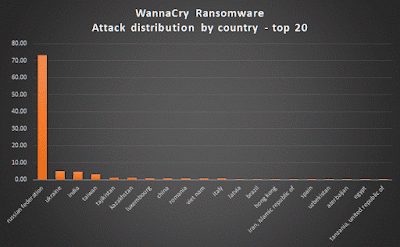
WannaCry or WannaCrypt Ransomeware is all we see people talking about this week. The cyber attack which started affected computers last Friday continues to spread in full swing and despite there being a patch by Microsoft, thousands of computers remain affected. The ransomware gives the hackers access to the complete system with all data - and in order to once again access their computers, users are asked to
pay $300 to $600 (between Rs 9,000 and Rs 38,000) worth
bitcoins in ransom..
As with every new threat, WhatsApp spammers are having a field day. There have been multiple messages shared over the messaging app, warning users to stay safe. While most of the messages give users a gist of what the attack is all about and ask them to follow certain measures, many are off the mark and completely ridiculous. Apart from warning users about the possible threats, there are even other "sources of malware" listed in the messages which are completely fake and could mislead readers. Here's a list of all the fake messages circulating on WhatsApp:.
1. No money withdrawls:
While the message below does contain some true facts, most of it is misrepresented though.
Over 150 countries have been affected, not merely 74. Also, banks are yet to issue an official statement regarding ATMs or other services.
Here's what one of the messages doing the rounds says: "Stay tunned with latest news for updates..
.Also keep antivirus ON and do not operate bank n shoping sites or pay utility through mobile hold on for today before doin anything.....Massive Ransomeware attack...Total 74 countries affected...Please do not open any email which has attachments with "tasksche.exe" file. Please send this important message to all your computer users ATM 's will be closed for next 2-3 days probably, due to ransomware cyber attack within India. So, if you need then please withdraw money today for rest of week atleast. Don't do any online transactions today. Please inform all contacts from your list not to open a video called the "Dance of the Hillary". It is a virus that formats your mobile. Beware it is very dangerous. Fwd this msg to as many as you can!.
Except africa all country's IT companies are hacked. Don't open any shopping carts today.
Please inform all contacts from your list not to open a video called the "Dance of the Hillary". It is a virus that formats your mobile. Beware it is very dangerous. They announced it today on BBC radio. Fwd this msg to as many as you can!".
2. Dance of Hillary:
The below message claiming a Dance of Hillary video file doing rounds is fake.
The Dance of Hillary is simply a renaming of Dance of Pope virus that circulated on smartphones. Though it is always advisable to exercise caution before downloading any file, this time around, this warning is a fake.
"Please inform all contacts from your list not to open a video called the "Dance of the Hillary". It is a virus that formats your mobile. Beware it is very dangerous. They announced it today on BBC radio. Fwd this msg to as many as you can!.
Massive Ransomeware attack...Total 74 countries affected...Please do not open any email which has attachments with "tasksche.exe" file.
The messages above are the main ones doing rounds. There is also another message circulating which explains the new malware in detail and is pretty accurate in the description:.
"What is Ransomware?
And How to be aware!.
True Information Here,
Ransomware is a malicious software that encrypts the files and locks device, such a.
a computer, tablet or smartphone and then demands a ransom to unlock it. Recently, a.
dangerous ransomware named 'Wannacry' has been affecting the computers worldwide.
creating the biggest ransomware attack the world has ever seen. This has affected.
What is WannaCry Ransomware?.
WannaCry ransomware attacks windows based machines.
It also goes by the name.
WannaCrypt, WannaCry, WanaCrypt0r, WCrypt, WCRY.It leverages SMB exploit in.
Windows machines called EternalBlue to attack and inject the malware. All versions of.
windows before Windows 10 are vulneable to this attack if not patched for MS-17-010.
After a system is affected, it encrypts the files and shows a pop up with a countdown and.
instructions on how to pay the 300$ in bitcoins to decrypt and get back the original files. If.
the ransom is not paid in 3 days, the ransom amount increases to 600$ and threatens the.
user to wipe off all the data. It also installs DOUBLEPULSAR backdoor in the machine.
What can you do to prevent infection?.
It has released a Windows security patch MS17-010 for Winodws machines.
This needs to be applied immediately and urgently.
Use This link : https://support.microsoft.com/en-in/help/4013078/title
Remove Windows NT4, Windows 2000 and Windows XP-2003 from production.
environments.
Block ports 139, 445 and 3389 in firewall.
Avoid clicking on links or opening attachments or emails from people you don't.
know or companies you don't do business with.
SMB is enabled by default on Windows. Disable smb service on the machine by.
going to Settings > uncheck the settings > OK.
Use this Link :https://support.microsoft.com/SMB
Make sure your software is up-to-date.
Have a pop-up blocker running on your web browser.
Install a good antivirus and a good antiransomware product for better security.
File Names:
@Please_Read_Me@.txt.
@WanaDecryptor@.exe.
@WanaDecryptor@.exe.lnk.
Please Read Me!.txt (Older variant).
C:\WINDOWS\tasksche.exe.
C:\WINDOWS\qeriuwjhrf.
131181494299235.bat.
176641494574290.bat.
217201494590800.bat.
[0-9]{15}.bat #regex
!WannaDecryptor!.exe.lnk.
00000000.pky.
00000000.eky.
00000000.res.
C:\WINDOWS\system32\taskdl.exe.
All must be aware of Massive Ransomeware attack.....Please do not open any email which has attachments with tasksche.exe. file... Pl spread across all possible groups and branches... Not to open email attachments from unknown sources and update AV patch urgently.
What's Next ? - No news regarding this so don't worry . :-P !