SAN stands for Subject Alternative Name certificates and allows you to secure multiple domain names with a single SSL certificate.
SAN is used where a single server can access with multiple domain address.
SAN : Through san you specify additional host names (sites, IP addresses, common names, etc.) to be protected by a single SSL Certificate, such as a Multi-Domain (SAN) or Extend Validation Multi-Domain Certificate.
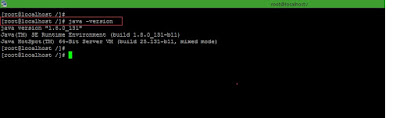
Step 1: Make sure you have installed java in our machine.
Command >>
java -version
Screenshot 1:
Step 2: Find installed java location.
Command >>
find / -name java
Screenshot 2:
Step 3: Locate to /bin folder of java.
Screenshot 3:
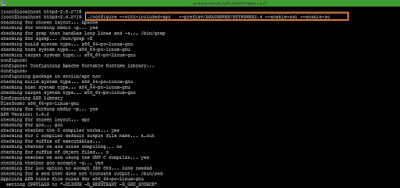
Step 4: Use below command to generate java keystore and self-signed certificate.
Command >>
./keytool -genkey -alias ssl -keyalg RSA -keystore keystore.jks -keysize 2048 -ext SAN=dns:uat.middbox.com,dns:uat.MB.com
Where, keytool >> Java Keytool is a key and certificate management utility.
-genkey >> Generate SSL certificates and certificate requests
-alias >> Name given to the certifiacte.
-keyalg >> Algorithm to be used in certificate.
-keystore >> SSL cert to be store in file.
-keysize >> RSA key size 2048 ( Certificate authorities will not sign csrs less than 2048 bits in size so you should generate your csr to be 2048 bits. )
-ext >> Extension attribute to provide dns and email details its optional to the certificate .
Screenshot 4:
Step 5: Use below command into keytool to create a CSR using existng keystore.jks.
Command >>
./keytool -certreq -alias ssl -keystore keystore.jks -file MiddBox.csr -ext SAN=dns:uat.middbox.com,dns:uat.MB.com
-certreq >> Generates a certificate request
-file >> CSR to be store in file.
Screenshot 5:
Step 6: Check which certificates are in a Java keystore available.
Commmand >>
./keytool -list -v -keystore keystore.jks
Screenshot 6:
Step 7: Check generated CSR using online CSE decoder website
https://certlogik.com/decoder/ .
Command >>
cat MiddBox.csr
Output :
-------------------------------------------------------------------------------------------------
-----BEGIN NEW CERTIFICATE REQUEST-----
MIIDEDCCAfgCAQAwczELMAkGA1UEBhMCSW4xDDAKBgNVBAgTA01haDEMMAoGA1UE
BxMDTXVtMRAwDgYDVQQKEwdNaWRkYm94MRYwFAYDVQQLEw1NaWRkbGV3YXJlQm94
MR4wHAYDVQQDExV1YXQubWlkZGxld2FyZWJveC5jb20wggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQCu1mxQDADQvRxBFYPkJ7GxcYTPIATqElOXgxX8E03A
FNUzPROplCr4UgcCUXo6LUMJGr/oPTlIzSyizMSYt4YSlti8Uw0AjLcai/EcgHOI
9Nu6Xm7A8KSd1gZJZuIdAj9HfoNbGmQvjATvYwYgdSdtkMpxwwk46tcALnDJwTIB
IWYY3eQC660BwrOOvjq8fqTLYrDhRlzhBMjFuqAd7sqQO2W5tMwrlYUZ6NoLVYHH
Uu5kej+axdQb4Q7kl7ULwaCtImrfGqJq8zM0/i/Qu/xPAydO8vopscI+fjJvJ3ix
a5ExHu0jKGJOcvlcizFxbYJiqy0502g+gAd+38bMr6HRAgMBAAGgWDBWBgkqhkiG
9w0BCQ4xSTBHMCYGA1UdEQQfMB2CD3VhdC5taWRkYm94LmNvbYIKdWF0Lk1CLmNv
bTAdBgNVHQ4EFgQUsW0GTWPc1w+S8oE9JPSUVV3eH4kwDQYJKoZIhvcNAQELBQAD
ggEBAGnRc3lshhh0zjkEmJdFJTEZx/XYc8ZMhLhpGAnGjCZVxWMnPJzd0O0Ayzyy
dyMM+C0rWefMEsZKUE4kQufycUigVVfohhze9XyL0+eCFznqUpBkF4eFKh4qetOr
ww9KpjA0vMCmhEFtwfd5BfS6+a/sMKLypVQDEGnAH1dMEfjUdkvNo72OwX25dIOC
oDTyzuX+BqDk99j52JQESmd7AIV2FbeszmURCCFHmds8bcopvtS3y1fsnwztS0OQ
mas/zbX3vgmR7Cx5Ac9QxreDx34G+9UM5Wo1vykc98R6uSbDPJOe0gyPDsa9Nt3C
A3UyYiiLX45YLq8LqLQtf2XH6t8=
-----END NEW CERTIFICATE REQUEST-----
-------------------------------------------------------------------------------------------------
Copy above encrypted code and paste into
https://certlogik.com/decoder/
Screenshot 7-1:
Screenshot 7-2:
Screenshot 7-3:
Reference link :
https://www.sslsupportdesk.com/java-keytool-commands/
Reference link :
https://www.sslshopper.com/what-is-ssl.html
Reference link :
https://www.digicert.com/ssl/
Reference link :
https://www.websecurity.symantec.com/
Thanks :-)